Securing Your Crypto Wallet

Why the world misses out on basic user-based security and isolation.
When it came time to create my CryptocurrencyOS, based on Linux Mint I wanted to solve some practical user and security issues. The end result was for people to have their own crypto wallets in a secure, opensource, environment and encourage more adoption of cryptocurrency. I applied some of my experience with some of the products I developed for compevo and Techrich.
The first problem is that a lot of people don’t even know how to find or download a wallet (at least safely, since there are a lot of fake / malware wallets that steal people’s coins). If they don’t know how to avoid the above, then how would they be able to secure their computer?
A lot of times it is better to start with a new, fresh and secure house that we know is safe rather than hoping we identify any potential holes or malware in the existing house.
Even professionals who are good with security, often don’t practice the best of security. For example most of you reading this are probably running their browser as the same user you use and login as.
If the browser is compromised via some sort of exploit whether Java, javascript, ActiveX, Flash or other executable payload, what happens then? The attacker gains instant access to your whole system, or at least everything in your user account which may include sensitive e-mails, picture, documents, intellectual property, passwords, keys etc..
But what if you were running as a different user? Say your username is “abcmainlogin” but your browser was running as “abcbrowserlogin”. As long as it is not a root or admin exploit, the attacker would have limited access to just your web browser profile and files.
I think running processes as isolated users is much safer and this is how most unix based systems work. However, even in Windows, Unix or Linux based Desktops, the majority of applications are running as your main user which is a security risk.
Furthermore, it is an incredible pain to create a brand new user account for each application, so most of us don’t do it. To make this happen you have to edit all of your Desktop icons/shortcuts to specify the correct user to run or sudo as.
sudo which originally stood for “superuser do” is a program that allows you to run a program with the permissions of another user. By default we associate sudo as being root, because that is the default, but there is a -u flag that allows you to run the application as any other user. sudo access is controlled by /etc/sudoers and allows you to fine grain whether or not a password is required to run sudo for particular commands or if there is any sudo access for a user at all. Most Linux Desktops are setup with the user you create during install being able to sudo to any command (kind of like the Administrator account in Windows).
Then from there, it’s not that simple itself. By default although sudo would run the user as itself, it would not run from its own home directory, it would use the home of the main/current user. That can be fixed easily enough with the -H flag, but then things still don’t work. The apps will need a specific .xauthority or they will not be able to run in your Desktop (Gnome). To fix that each user needs access to your main user’s .xauthority file which must also be passed as the XAUTHORITY= flag to sudo and correct permissions must be assigned so the users can access it.
An example of running as a different user on CryptoCurrency OS is below, notice it says “as ETH-Ethereum-Mist”, which means the wallet application is running as a different user than the logged in Desktop user:
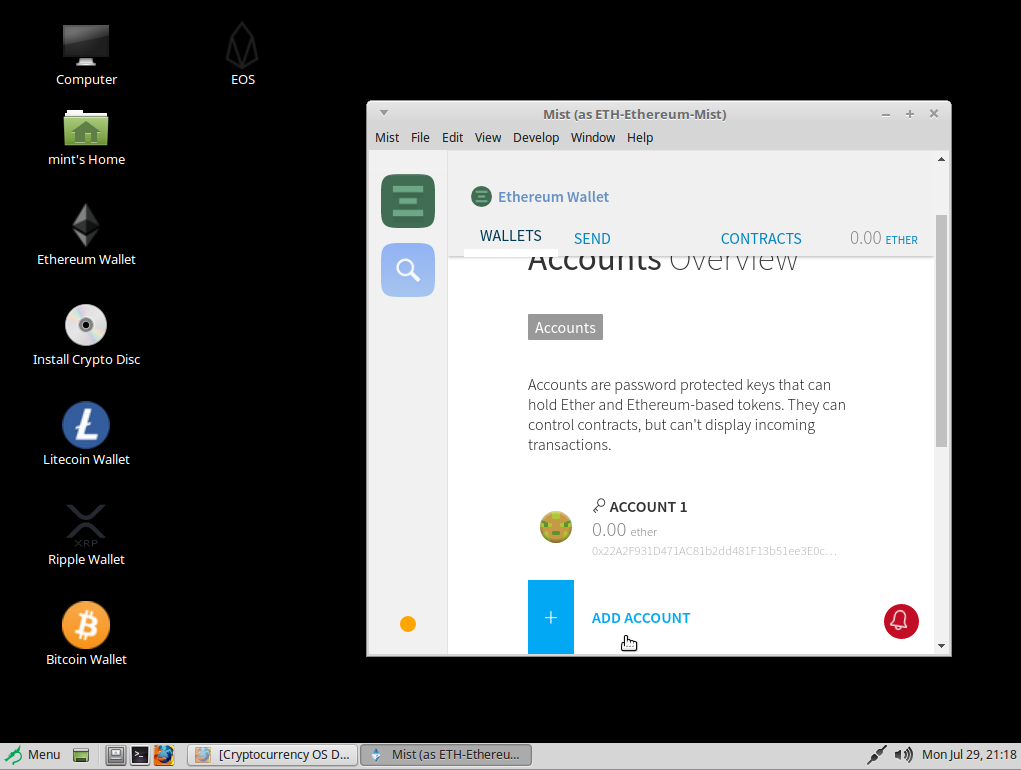
How To Automate Specific Binaries to run as other users from the GUI
1.) CSV File
A simple CSV file like this will do (it could be a database if you were doing this in a larger scale):
Field Explanation
Shortcut/Friendly Name, Path/To/Binary, Any Arguments To Pass, Icon path
Bitcoin Wallet,BTC-Bitcoin-Electrum/electrum-3.3.6-x86_64.AppImage,,BTC.png EOS,EOS-SimplEOS/simpleos-0.6.9-x86_64.AppImage,,EOS.png Ethereum Wallet,ETH-Ethereum-Mist/mist,--syncmode nosync,ETH.png Litecoin Wallet,LTC-Litecoin-Electrum/electrum-ltc-3.3.5.1-x86_64.AppImage,,LTC.png Ripple Wallet,XRP-Toast/ToastWallet-2.3.10-x86_64.AppImage,,XRP.png Digibyte Wallet,DGB-Digibytes/digibyte-7.17.2/bin/digibyte-qt,,DGB.png
2.) Script To Make/Modify Shortcuts
#!/bin/bash echo y|mv /usr/lib/linuxmint/mintMenu/applications.list /usr/lib/linuxmint/mintMenu/applications.list-old basewalletdir=/wallets/ IFS=$(echo -en "\n\b") for entry in `cat shortcuts.csv`; do echo "entry=$entry" programname=`echo $entry|cut -d "," -f 1` binaryoptions=`echo $entry|cut -d "," -f 3` binarypath=`echo $entry|cut -d "," -f 2` username=`echo $binarypath|cut -d "/" -f 1` icon=`echo $entry|cut -d "," -f 4` #echo "programname=$programname binary=$binarypath $binaryoptions user=$username" template=$(cat << SETVAR [Desktop Entry] Name=$programname Exec=sudo -u $username -H XAUTHORITY=/wallets/.Xauthority /wallets/$binarypath $binaryoptions Terminal=false Type=Application Categories=Finance;Network; Icon=/wallets/icons/$icon SETVAR ) echo -e "$template" > /usr/share/applications/$programname.desktop mkdir -p /etc/skel/Desktop echo -e "$template" > /etc/skel/Desktop/$programname.desktop chmod 755 /etc/skel/Desktop/$programname.desktop #update favorite shortcuts echo "location:/usr/share/applications/$programname.desktop" >> /usr/lib/linuxmint/mintMenu/applications.list #don't edit this file because it doesn't work: /home/mint/.linuxmint/mintMenu/applications.list done chmod 755 /wallets/icons -R
3.) Script to create user accounts
#!/bin/bash basedir=`pwd` for walletdir in `ls -d */`; do walletdir=`echo $walletdir|cut -d "/" -f 1` #use max uid of 499 otherwise the users will show on login screen sudo useradd -b $basedir $walletdir -s /bin/false -K UID_MIN=200 -K UID_MAX=499 sudo chown -R $walletdir.$walletdir $walletdir sudo chmod 700 -R $walletdir done
But this was my philosophy of basic user-based security when I created the CryptocurrencyOS. The main user has sudo access without a password (although they could change this to require a password) but the main point is that they are sudoing to run each cryptocurrency wallet as a different user. Each wallet has its own user account and separate home directory so that a compromise of one could not compromise the other.
In a world with more and more exploits, malware and essentially where things are untrusted, this is a good middle ground to help protect yourself. Of course there are always containers and virtual machines, but it is not realistic for most users to be running containers and virtual machines just to run a few applications.
I think this is where things need to head for the next level of security, especially in the Desktop userspace. It would be good if most applications could run as a different user to limit potential damage in the event that your machine is exploited or hacked. This is an excellent opportunity in the future for modern Desktop UI’s to have built-in security options like the above, but for now we can all write our own customizations and scripts to achieve more security.
The future is better with increased security, and one day, more and more distros will probably switch to this sort of approach and a more native way to do it will be made.
To see the above in action you can download the free Opensource Cryptocurrency OS from https://cryptocurrencyos.org
Cheers,
Areeb




